In general, we want to protect the operating system from access by user programs, and, in addition, to protect user programs from one another. This protection must be provided by the hardware. It can be implemented in several ways. Here, we outline one such possible implementation.
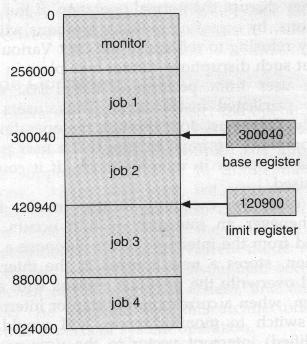
What is needed to separate each program's memory space is an ability to determine the range of legal addresses that the program may access, and to protect the memory outside that space: We can provide this protection by using two registers, usually a base and a limit, as illustrated in the figure below. The base register holds the smallest legal physical memory address, and the limit register contains the size of the range. For example, if the base register holds 300040 and limit register is 120900, then the program can legally access all addresses from 300040 through 420940 inclusive.
Hardware address protection with base and limit registers.
The base and limit registers can be loaded by only the operating system, which uses a
special privileged instruction. Since privileged instructions can be executed only in
monitor mode, and since only the operating system executes in monitor mode, only the
operating system can load the base and limit registers. This scheme allows the monitor to
change the value of the registers, but prevents user programs from changing the registers'
contents.
The operating system, executing in monitor mode, is given unrestricted access to both monitor and users' memory. This provision allows the operating system to load users' programs into users' memory, to dump them out in case of errors, to access and modify parameters of system calls, and so on.
Last Updated Jul.29/99